6. Testbed
6.1. Testcase
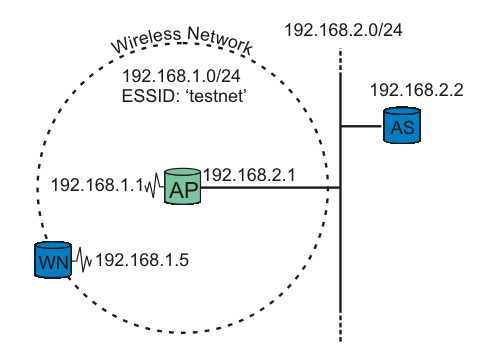
figure testbed: A wireless node request authentication.
Our testbed consists of two nodes and one Access Point (AP). One node functions as the Supplicant (WN), the other as the back-end Authentication Server running RADIUS (AS). The Access Point is the Authenticator. See figure testbed for explanation.
 | It is crucial that the Access Point be able to reach (ping) the Authentication Server, and vice versa! |
6.2. Running some tests
Running some tests
The RADIUS server is started in debug mode. This produces a lot of debug information. The important snippets are below:
- Default EAP type is set to PEAP.
- RADIUS's TLS settings are initiated here. The certificate type, location, and password are listet here.
- Inside the PEAP tunnel, MS-CHAPv2 is used.
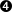
- The username/password information is found in the users file.
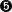
- RADIUS server started successfully. Waiting for incoming requests.
The radius server is now ready to process requests!
The most interesting output is included above. If you get any error message instead of the last line, go over the configuration (above) carefully.
Now the Supplicant is ready to get authenticated. Start Xsupplicant in debug mode. Note that we'll see output produced by the two startup scripts: startup.sh and startup2.sh.
# xsupplicant -c /usr/local/etc/1x/1x.conf -i eth0 -d 6 Starting /etc/1x/startup.sh Finished /etc/1x/startup.sh Starting /etc/1x/startup2.sh Finished /etc/1x/startup2.sh
At the same time, the RADIUS server is producing a lot of output. Key snippets are shown below:
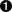
- TLS session startup. Doing TLS-handshake.
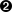
- The TLS session (PEAP-encrypted tunnel) is up.
- The Supplicant has been authenticated successfully by the RADIUS server. An "Access-Accept" message is sent.
- The MS-MPPE-Recv-Key [RFC2548 section 2.4.3] contains the Pairwise Master Key (PMK) destined to the Authenticator (access point), encrypted with the MPPE Protocol [RFC3078], using the shared secret between the Authenticator and Authentication Server as key. The Supplicant derives the same PMK from MK, as described in Key Management.
The Authenticator (access point) may also show something like this in its log:
00:02:16 (Info): Station 0002a56fa08a Associated 00:02:17 (Info): Station=0002a56fa08a User="testuser" EAP-Authenticated
That's it! The Supplicant is now authenticated to use the Access Point!